The network segmentation test report should include a test start date test completion date results and recommendations. Hak5 industry leading hacker tools award winning hacking shows for red teams pentesters cyber security students and IT professionals.

How To Set Up A Pentesting Lab Rapid7 Blog
Penetration testing is the practice of launching authorized simulated attacks against computer systems and their physical infrastructure to expose potential security weaknesses and vulnerabilities.
. Home to an inclusive information security community. Established in 2005 LGMS is accredited with multiple international certifications that makes it a leading cyber security penetration testing and assessment firm in the Asia Pacific region. Once you have finished testing your network segmentation you should provide a detailed report of these tests.
Change your host file to access the Linux system under the following names. We also do tutoring from CP primary to baccalaureats grade. Write an HTTP client to retrieve the home page of your site using an http library for example nethttp in ruby.
A penetration test also called a pen test or ethical hacking is a cybersecurity technique organizations use to identify test and highlight vulnerabilities in their security postureThese penetration tests are often carried out by ethical hackers. Look at it this way just like a hack into the organizations software can disrupt its operations so also can penetration testing cause disruption. Practical network penetration tester pnpt Standalone exam 299.
Build a centralized repository of your companys assets that can be easily searched sorted and filtered to provide full visibility into your attack surface. These in-house employees or third parties mimic the strategies and actions of an attacker in order to evaluate. Versions and do OS fingerprinting in a single TCP port checkInspect Top 100 TCP ports for free or get a paid plan to automate and schedule extensive custom scans for even more ports.
Install Apache inside your vm change the home page of the hosted site using vim. If your asset is public-facing the Internet or private ie behind a firewall within the network with controlled access. A penetration tester sometimes called an ethical hacker is a security pro who launches simulated attacks against a clients network or systems in order to seek out vulnerabilities.
As a minimum the network segmentation test report should include the following sections. Please note we will not be able to troubleshoot or support local VM issues or. Awesome Penetration Testing.
We teach children and adults English and French to take exams such as DALF DELF TOEIC TOEFL IELTS. A collection of awesome penetration testing and offensive cybersecurity resources. Creators of the WiFi Pineapple USB Rubber Ducky more.
Our servers have a fast Internet connection and speed. Each Nmap port scan against a target IP address or hostname automatically maps the attack surface and gives accurate data for your. Access this page in your browser on the host.
Sub-domains DNS open ports HTTP headers risk score etc to CSV XLS or PDF format. A place to learn and improve penetration testingethical hacking skills for FREEThe labs consist of 30 real world scenarios to practice the latest exploits and cutting edge hacking techniques. Even if you have the right toolset on your machine the networks local firewall can still stop you from scanning external hosts.
Launch Firefox browser and navigate to home it should auto-launch. Our penetration testing process covers the attempts to gain privileged access to firewalls networks and respective devices servers IoT web applications and other points of exposure will be conducted in a safe and controlled manner while. Hak5 industry leading hacker tools award winning hacking shows for red teams pentesters cyber security students and IT professionals.
This approach helps in drastically reducing the time spent to prioritize vulnerabilitiesLets discuss each point in detail. Export your entire attack surface inventory ie. Find open ports and running services incl.
Now when the victim will try to access our share folder therefore he will try of connecting with us through his network IP given below image is a proof to demonstrate that victim is connecting malicious IP. Creators of the WiFi Pineapple USB Rubber Ducky more. A Leading Cyber Security Penetration Testing Firm.
The standalone exam is perfect for students who are already well-versed in OSINT external penetration testing techniques such as vulnerability scanning information gathering password spraying credential stuffing and exploitation and internal penetration testing techniques such as LLMNR Poisoning NTLM. The project aims for a wide spread of goals ranging from network analysis stress tests sniffing vulnerability assessment computer forensic analysis exploitation privilege escalation and more. Test the effectiveness and resiliency of enterprise assets through identifying and exploiting weaknesses in controls people processes and technology and simulating the objectives and actions of an attacker.
Whatever your need in getting your projet done or documents we are experienced enough to provide you with. Get instant access to custom vulnerability scanners and automation features that simplify the pentesting process and produce valuable results. Should you discover a vulnerability please follow this.
Public assets usually carry a higher risk but that does not always mean they should be prioritized. KNFormation is a FREELANCE company allowing you to study at home. Turla surveys a system upon check-in to discover active local network connections using the netstat -an net use net file and net session commands.
Tropic Trooper has tested if the localhost network is available and other connection capability on an infected system using command scripts. At Firmus our penetration testing services leverage a hybrid approach composed of automated and manual testing methods. Home to an inclusive information security community.
Two forms of 247 immediate contact such as cell phone pager or home phone if possible One form of secure bulk data transfer such as SFTP or encrypted email Note. The platform helps you cover all the stages of an engagement from information gathering to website scanning network scanning exploitation and reporting. Signing up and getting started takes only minutes once you make your choice.
What is a pen test. Follow the lab 0 instructions to ensure that you have an Azure account and active subscription. Just like in the case of whether penetration testing can break a system in this case it is crucial to understand that penetration testing can disrupt an organizations network of operation.
The number for a group such as the help desk or operations center can replace one emergency contact but only if it is staffed 247.

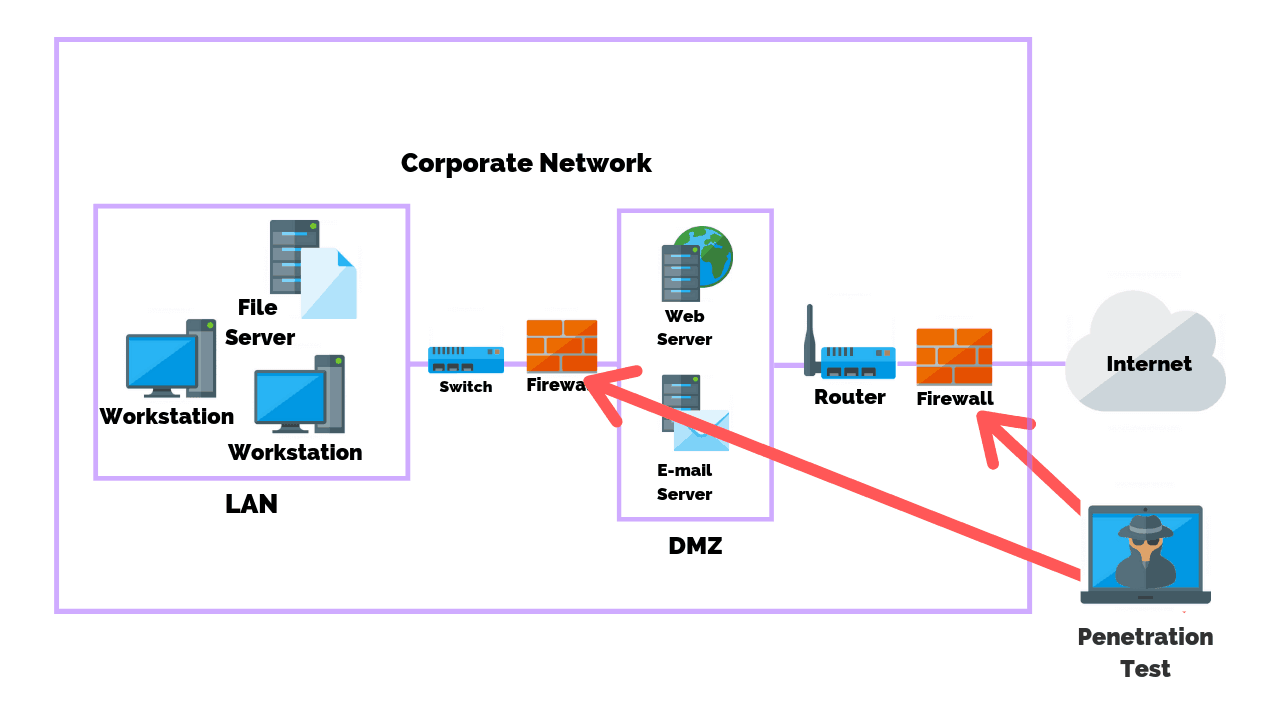
Firewall Penetration Testing Steps Methods Tools Purplesec
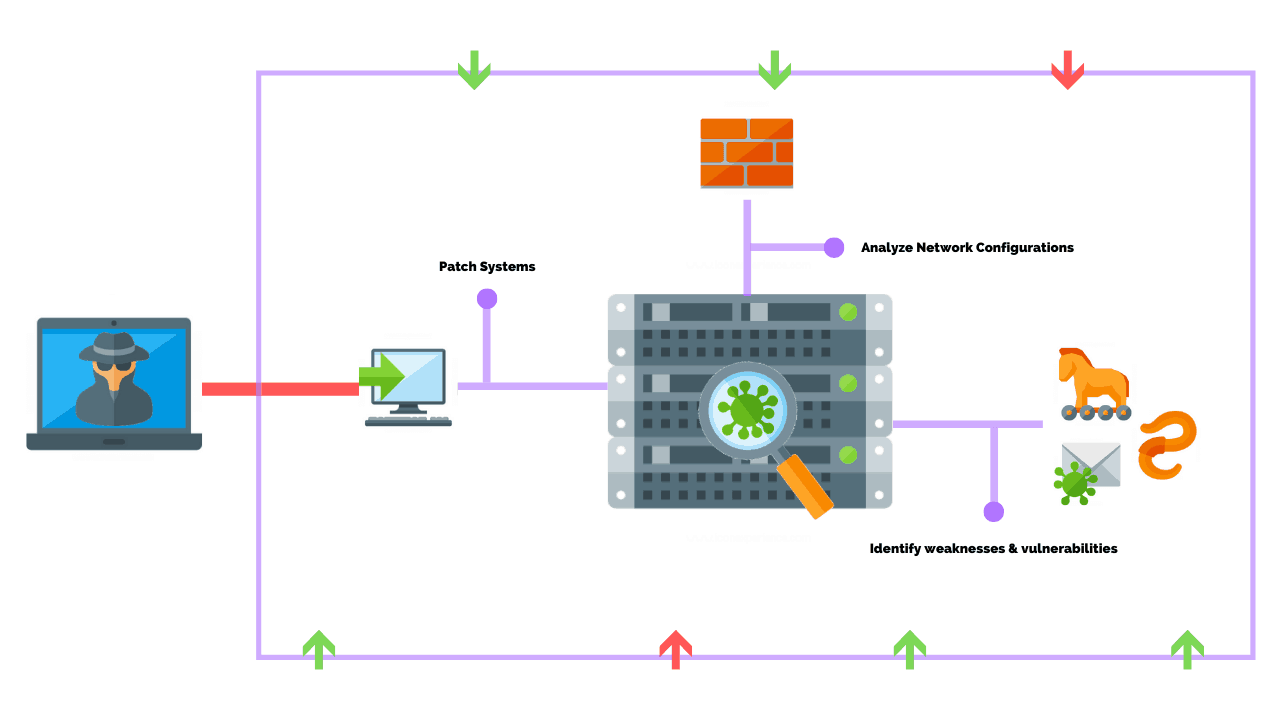
How To Perform A Successful Network Penetration Test Purplesec

Ultimate Guide On How To Perform A Successful Network Penetration Test
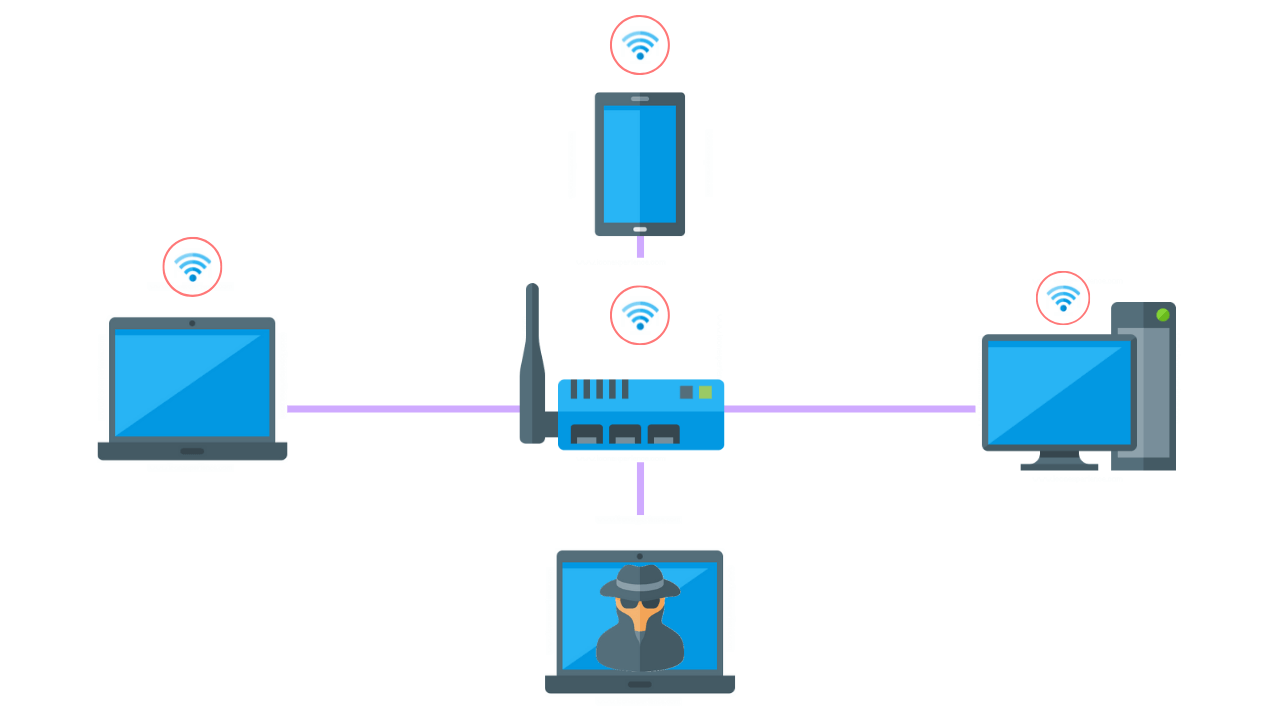
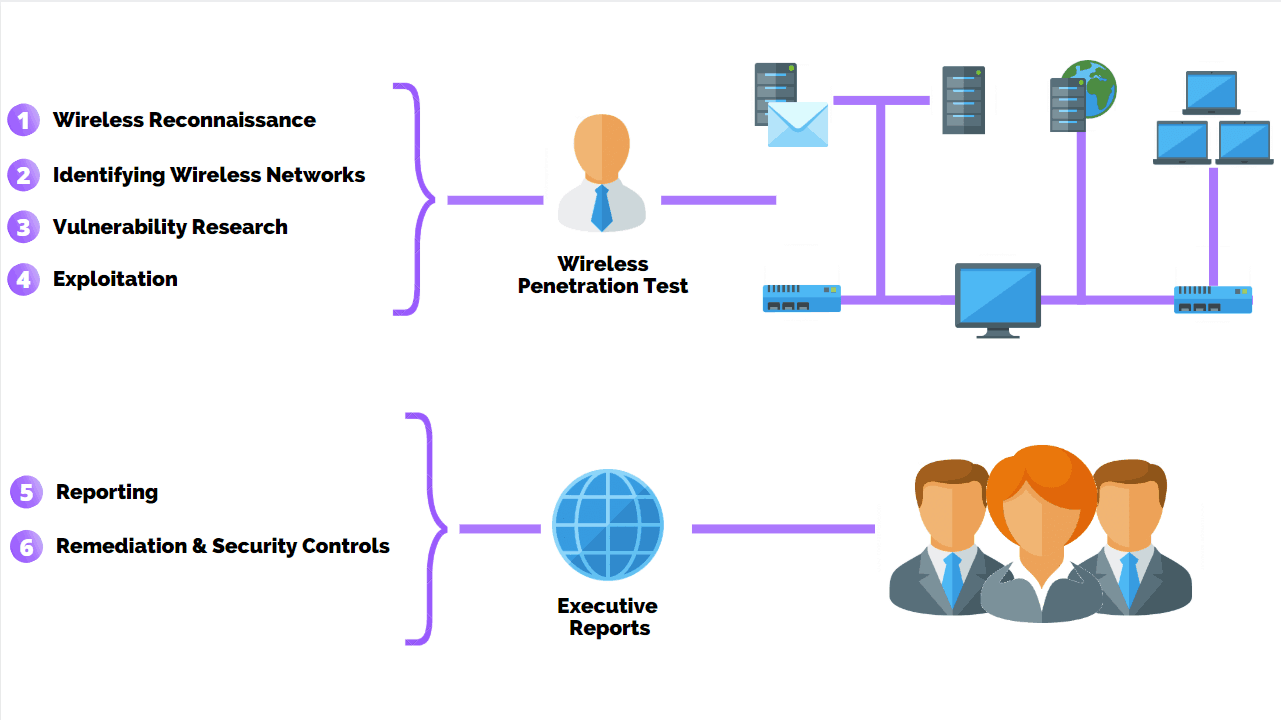
How To Perform A Successful Wifi Penetration Test
Building A Test Lab For Pentesting Guide White Oak Security

0 comments
Post a Comment